
Just last week, the TechRepublic website posted an article detailing a business software vulnerability that is being actively exploited by ransomware groups and state-sponsored cyberespionage threat actors.
The products are PaperCut NG and PaperCut MF print management software, and the vulnerability allows unauthenticated users to execute malicious code remotely without credentials. That’s according to a joint Cybersecurity Advisory (CSA) from the FBI and CISA.
That CSA mentions that users began exploiting the vulnerability as early as the middle of April and continue to exploit it today. That’s in spite of the fact that PaperCut posted a software patch in March and has been updating it since.
TechRepublic estimates that up to 70,000 organizations could be targeted by malicious actors.
To PaperCut’s credit, the company has a banner on its website announcing an urgent security message. The company says on the announcement page that it has evidence to suggest that unpatched servers are being exploited in the wild.
We have to interrupt this blog post to reiterate one of the basic steps companies can take to bolster their cyber security stance: Keep software and firmware patched and up-to-date to protect against known vulnerabilities.
There’s really no excuse for system administrators to leave servers vulnerable two months after a patch has been released.
And now, back to the blog.
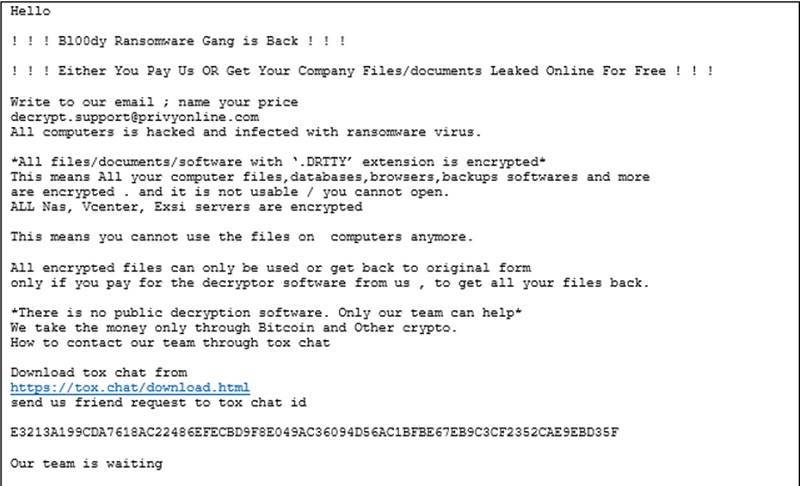
One of the attacks the FBI has documented involves the ‘Bl00dy Ransomware Gang.’ The gang exploited the PaperCut vulnerability to gain access to networks. Then the gang exfiltrated and encrypted the data on those systems. They left ransom notes on victim systems demanding payment in exchange for decryption of encrypted files.
Notes like this:
For the organizations that have yet to patch their systems, the FBI suggests focusing detection efforts on three key areas:
- Network traffic signatures – Look for network traffic attempting to access the SetupCompleted page of an exposed and vulnerable PaperCut server.
- System monitoring – Look for child processes spawned from a PaperCut server’s pc-app.exe process.
- Server settings and log files – Look for evidence of malicious activity in PaperCut server settings and log files.
The agency goes on to say that even these methods may fail to detect malicious activity.
At this point we have to mention that LRS has a division that develops and sells output management software, LRS Output Management. That division constantly tests its software for vulnerabilities that could be exploited. The software has been rock solid throughout its history.
For PaperCut customers that are not interested in replacing their print management software, contacting our security team is a good idea. Our security experts can help detect intrusions and help remediate your security vulnerabilities.
At the very least, apply all security patches to all your software.